Umbra Log is a personal logging system designed to provide a secure and reliable way to record sensitive information, personal notes, and important decisions. Every log entry is encrypted using strong cryptographic algorithms, ensuring that the contents are protected from unauthorized access. This encryption, combined with tamper-evident features, guarantees that any modifications to your records can be detected, preserving the integrity of your logs. Whether documenting professional actions, personal reflections, or time-sensitive events, Umbra Log offers a trusted framework for maintaining accurate, verifiable records without fear of accidental deletion or compromise.
Unlike conventional note-taking applications, Umbra Log is built with advanced security principles in mind. Its architecture separates data storage from key management, storing encryption keys on a portable USB key drive rather than on the device itself. This approach ensures that even if your computer or mobile device is compromised, the encrypted logs remain inaccessible to anyone without the proper credentials. Password protection, coupled with strong cryptographic key derivation, ensures that only the authorized user can unlock and read the logs.
In addition to encryption, Umbra Log provides a structured and consistent way to organize entries, supporting both chronological and contextual tracking. Each record is linked to metadata that captures creation time, modifications, and other relevant details, allowing for secure auditing and accountability. The system also facilitates backups and secure transfers of the log data without compromising confidentiality, giving users full control over their personal archive.
Umbra Log is particularly well-suited for professionals, researchers, or anyone who needs a dependable method for recording private information. Its combination of encryption, tamper evidence, and portable key management makes it an ideal solution for maintaining privacy, ensuring integrity, and providing peace of mind that sensitive records are securely preserved over time.
Purpose
Umbra Log is designed to support personal accountability by providing a secure, tamper-resistant record of your actions and decisions. It is particularly useful for individuals who need to maintain reliable documentation of events, whether for personal reflection, professional reference, or legal purposes. Each entry is securely encrypted, ensuring that sensitive information remains confidential and protected from unauthorized access or accidental deletion.
The system’s design emphasizes integrity, meaning that every log is tamper-evident. Any attempt to alter or remove entries can be detected, giving users confidence that the records accurately reflect the original data. This feature makes Umbra Log a practical tool for situations where verifiable proof of actions is required, such as workplace documentation, research notes, or even informal accountability tracking.
By combining strong encryption with portable key management, Umbra Log ensures that only the authorized user can access the data, even if the device storing the logs is compromised. This approach provides a reliable digital record of personal or professional actions, effectively serving as a “cover-your-ass” solution. Users can safely document sensitive decisions, track progress, or maintain historical records without fear that their logs could be lost, altered, or exposed.
In essence, Umbra Log is more than a note-taking application; it is a secure, accountable system that preserves both privacy and integrity, giving users verifiable control over their own records and a dependable way to maintain digital accountability.
How It Works
USB Key-Based Encryption
All Umbra Log entries are secured through a dedicated encrypted key container stored on a USB drive, commonly referred to as a key drive. This key drive contains the cryptographic keys necessary to encrypt and decrypt your logs, ensuring that your data remains inaccessible to anyone without the proper credentials. In addition to the keys themselves, the container holds metadata detailing the key drive owner, creation date, and other relevant information, providing context and traceability for the secure storage.
The key drive also maintains an audit log of all access attempts, allowing you to track when and how the keys have been used. This makes it possible to verify that no unauthorized access has occurred and to review the history of interactions with the key container. To support proper use and security, the drive includes detailed instructions and a README, guiding users on safe handling practices and backup procedures.
By keeping the encryption keys physically separate from your main device, Umbra Log minimizes the risk of data compromise in case your computer is lost, stolen, or infected with malware. The separation ensures that even if someone gains access to the device where logs are stored, they cannot decrypt the data without the key drive. This approach provides strong security and portability, giving users confidence that their sensitive records are protected while remaining accessible whenever needed.
Encrypted Container
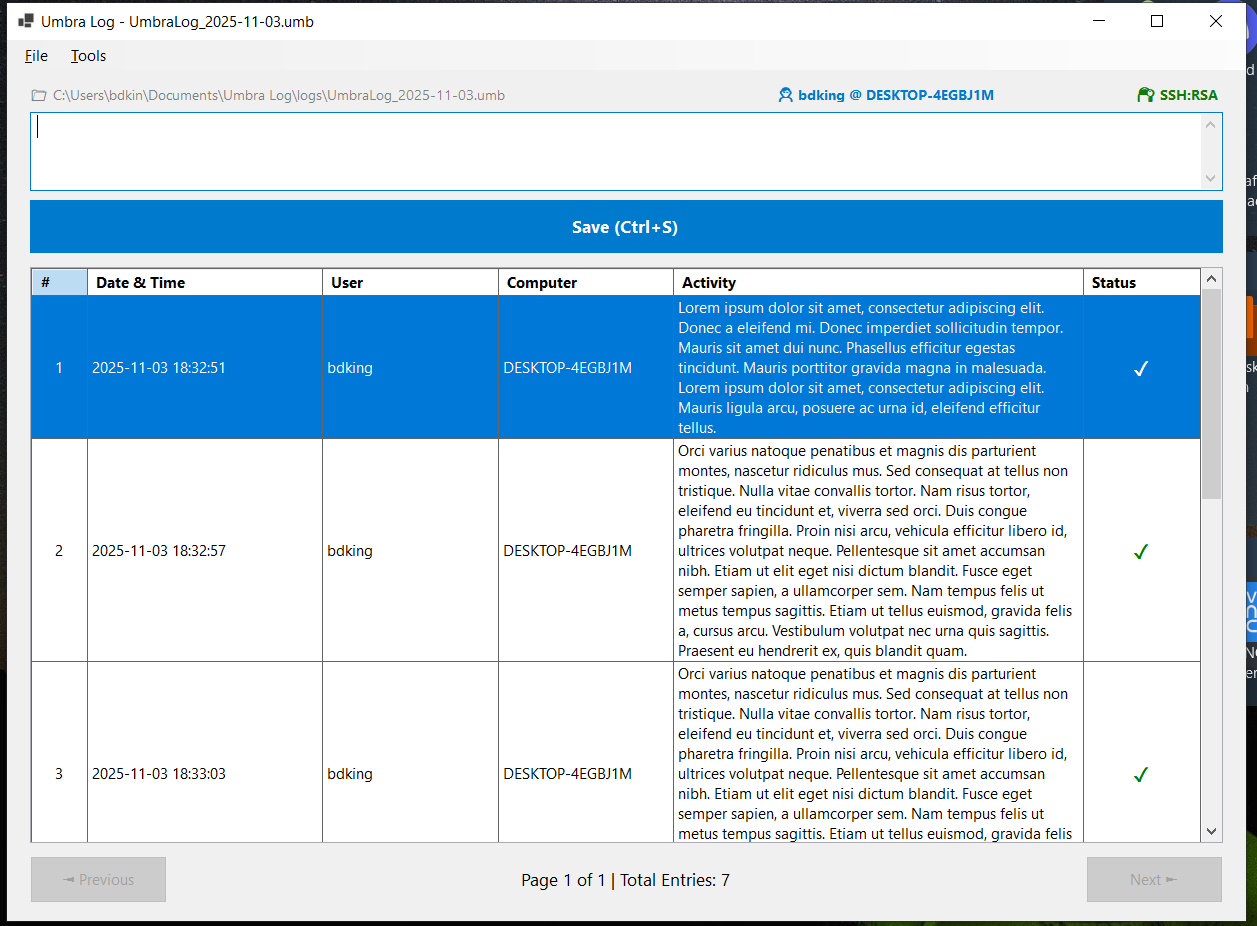
Umbra Log stores all log entries in a structured, encrypted JSON file. This file contains all your entries, along with authentication and integrity data, ensuring the logs remain private, tamper-evident, and verifiable. Each JSON file includes a version identifier and a format description to support compatibility and future updates.
The authentication section stores the username, a salted and iterated password hash, and the number of key derivation iterations used. This memory-hard hashing process makes it extremely difficult for attackers to guess or brute-force the password, even if they obtain the file.
Each entry in the JSON file contains a sequential entry number, a timestamp in UTC, the username and host that created the entry, the content itself, and a cryptographic hash. Each entry’s hash is calculated using the content and the previous entry’s hash, creating a chain that makes tampering detectable. Any modification to an entry breaks the chain, ensuring that all changes to the logs are evident. The “RecoveryStub” field is reserved for controlled recovery operations without exposing sensitive data.
Because the entire file is encrypted using keys stored on a separate USB drive, the logs cannot be decrypted without both the password and the key. This separation of data and keys adds an extra layer of security: even if the computer storing the JSON file is compromised, your logs remain safe.
This JSON-based approach combines strong encryption, verifiable integrity, and password protection while keeping the system portable and simple. Users can back up the encrypted JSON file, move it to another device, or maintain multiple copies without exposing the contents, ensuring a secure and reliable record of personal or professional activity.
{
"Version": "3.0",
"Format": "UmbraLog JSON v3 (UTC)",
"Auth": {
"Username": "demo_user",
"PasswordHash": "EXAMPLE_HASH_BASE64==",
"Salt": "EXAMPLE_SALT_BASE64==",
"Iterations": 100000
},
"Entries": [
{
"EntryNumber": 1,
"TimestampUtc": "2025-11-21T14:00:00Z",
"Username": "demo_user",
"Hostname": "DEMO-PC",
"Content": "This is the first log entry in Umbra Log.",
"PreviousHash": "GENESIS",
"Hash": "EXAMPLE_ENTRY_HASH_HEX",
"RecoveryStub": ""
},
{
"EntryNumber": 2,
"TimestampUtc": "2025-11-21T15:30:00Z",
"Username": "demo_user",
"Hostname": "DEMO-PC",
"Content": "Second log entry with some test content.",
"PreviousHash": "EXAMPLE_ENTRY_HASH_HEX",
"Hash": "EXAMPLE_NEXT_HASH_HEX",
"RecoveryStub": ""
}
]
}
Umbra Log JSON File Structure
Umbra Log stores all entries in a single encrypted JSON file. The file includes metadata about the log, authentication information, and the chronological list of log entries. Each field has a specific purpose to ensure security, integrity, and recoverability.
Version
Indicates the version of the Umbra Log format. This helps the application understand how to read and interpret the file. For example, "3.0" corresponds to the latest JSON structure with UTC timestamps and cryptographic features.
Format
A human-readable description of the format, e.g., "UmbraLog JSON v3 (UTC)". This clarifies which file format and encoding are in use.
Auth
Contains authentication data used to protect access to the log file.
Username— The account name associated with this log.PasswordHash— A salted cryptographic hash of the user’s password, which protects against unauthorized access.Salt— A random value used in the password hashing process to prevent attacks like rainbow tables.Iterations— The number of hashing iterations applied to the password to increase security.
Entries
An array of individual log entries. Each entry contains the following fields:
EntryNumber— A sequential identifier for the entry, starting at 1.TimestampUtc— The exact time the entry was created, recorded in Coordinated Universal Time (UTC) to ensure consistency across devices.Username— The account or user that created the entry.Hostname— The computer or device name where the entry was made.Content— The actual log text or record. This can be personal notes, observations, or any tracked information.PreviousHash— The cryptographic hash of the previous entry. This creates a chain linking each entry to the one before it, providing tamper-evidence. If an earlier entry is altered, subsequent hashes will no longer match.Hash— The cryptographic hash of the current entry, calculated from its content, metadata, andPreviousHash. This ensures the integrity of the log entry itself.RecoveryStub— An encrypted version of the previous hash or a derivative of it. It allows the application to recover or validate entries if the log file is partially corrupted while keeping sensitive data secure.
This structure ensures that Umbra Log is not only secure and encrypted but also tamper-evident and recoverable. Each entry is cryptographically linked, and sensitive information is protected both in transit and at rest. The combination of authentication, chained hashes, and encrypted recovery stubs makes the log suitable for personal accountability and verifiable record-keeping.
Audit Trail
Key Features
- Encrypted, tamper-evident personal logs
- USB-based key storage for portable, secure access
- Full audit trail for accountability
- Metadata and recovery instructions included
- Cross-platform compatible without needing admin privileges
- Backup support for extra key drives
Security Recommendations
- Use a strong, unique password (12+ characters).
- Keep the key USB drive in a safe place.
- Maintain a backup of the key drive separately.
- Do not leave the USB drive connected to your computer unattended.
- Review your audit logs periodically to ensure integrity.
Why Use Umbra Log?
Umbra Log is ideal for anyone who needs a secure, personal record-keeping system. Whether documenting sensitive work, personal events, or decisions, Umbra Log ensures that your logs are:
- Secure — protected from unauthorized access
- Portable — encryption keys stored on a USB drive
- Auditable — every access is recorded
- Tamper-evident — any changes are detectable
For personal accountability, peace of mind, or CYA purposes, Umbra Log provides reliable, encrypted record-keeping you can trust.

Wow, Bryan! I’m not computer literate enough to understand it all, but I am still so impressed. I hope this opens up new doors for you!