In the era of remote work, cybersecurity has never been more important. From phishing scams to ransomware, protecting your home office is crucial. Learn the best practices for securing your devices, networks, and data, ensuring your remote work environment stays safe from cyber threats.
Category: Cybersecurity
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, theft, and damage. It involves a range of technologies, processes, and practices designed to safeguard sensitive information, ensure privacy, and maintain the integrity of IT infrastructure. By implementing robust security measures, organizations and individuals can defend against cyber threats and ensure the safe and secure operation of their digital environments.
The Essential Guide to Understanding the Zero Trust Security Model: Why It’s Critical for Today’s Cybersecurity
The Zero Trust Security Model is transforming how organizations approach cybersecurity. By assuming that no one—inside or outside the network—should be trusted by default, it provides a robust framework for safeguarding sensitive data and mitigating evolving cyber threats. Learn why Zero Trust is critical for today’s digital world.
How AI is Reshaping Cybersecurity: Emerging Threats and Powerful Defenses
Artificial Intelligence (AI) is transforming the cybersecurity landscape, offering both advanced defense mechanisms and new threats. This article explores how AI is used in cyberattacks, how organizations can defend themselves, and the ethical challenges of AI in security. Learn how AI is changing the face of cybersecurity.
The Dark Web Unveiled: What Lies Beneath the Internet’s Shadowy Depths
Beneath the internet we know lies the Dark Web—a shadowy realm of anonymity powered by Tor. From whistleblowers to illicit markets like Silk Road, it’s a digital Wild West. Unravel its mysteries, myths, and what it means for our world in this deep dive into the unknown.
Unlocking the Secrets to Unbreakable Passwords: Your Ultimate Guide to Online Security
Creating strong, unique passwords is crucial for protecting your online accounts from cyber threats. This guide breaks down the best practices for crafting unbreakable passwords, avoiding common mistakes, and using security tools like MFA and password managers to keep your digital identity safe. Stay secure—learn how today!
The Dark Side of Smart Tech: How IoT Devices Are Putting You at Risk (And How to Fight Back)
The Internet of Things (IoT) is making life more convenient—but at what cost? From hacked security cameras to compromised smart home devices, the risks of connected tech are real. Learn how cybercriminals exploit IoT vulnerabilities and what you can do to protect yourself from digital threats.
Phishing Frenzy: How to Spot and Avoid Online Scams
Phishing attacks are a growing threat in today’s digital world. Learn how to spot and avoid online scams with our comprehensive guide. From recognizing phishing attempts to protecting your personal information, this article helps you stay one step ahead of cybercriminals.
The Password Debate: Why Length Beats Frequent Changes Every Time
Struggling with password security? Discover why longer passwords outperform frequent resets in protecting your digital life. Learn about the flaws of outdated policies, the power of passphrases, and modern tips like multi-factor authentication to secure your accounts without the hassle of constant password changes.
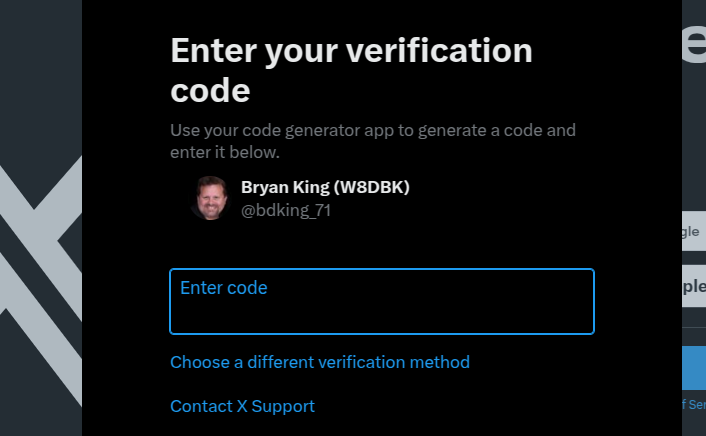
How My X Account Got Hacked—And I Still Can’t Get It Back
In January, my X (formerly Twitter) account was hacked, and even after resetting my password, I still can’t get back in. The hacker enabled two-factor authentication (2FA) with their phone number, blocking me from logging in. X support has been unhelpful, leaving my account in someone else’s hands.
Why Victims Are Hesitant to Report Cybercrime – And How This is Hindering the Fight Against Cybercriminals
Victims’ reluctance to report cybercrime is hindering efforts to combat cybercriminals, particularly in ransomware cases. Legal concerns, insurance implications, and reputational damage prevent many from cooperating with authorities. Learn about the impact of non-cooperation and strategies to foster victim transparency in the fight against cybercrime.