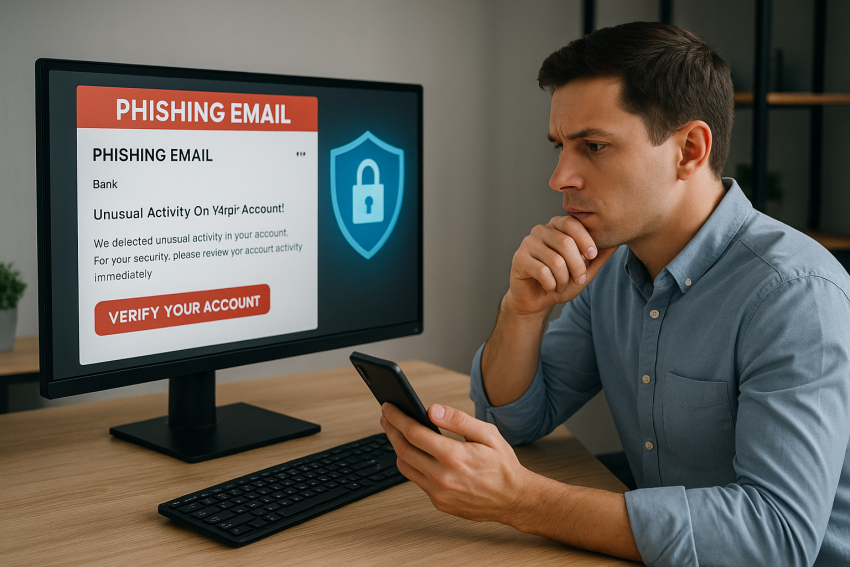
Ethical hackers are the unsung heroes in the battle against cybercrime. Learn how these digital defenders use their skills to expose threats before criminals strike—and how you can protect yourself in the process. This guide dives deep into real strategies, tools, and personal cybersecurity tips.
Category: Cybersecurity
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks, theft, and damage. It involves a range of technologies, processes, and practices designed to safeguard sensitive information, ensure privacy, and maintain the integrity of IT infrastructure. By implementing robust security measures, organizations and individuals can defend against cyber threats and ensure the safe and secure operation of their digital environments.
They Want Total Control: The Scary Truth About the SSA Phishing Scam That’s Hijacking Your Life
Hackers are impersonating the Social Security Administration in a new phishing scam that installs ScreenConnect malware to take full control of your device. Learn how to spot these attacks, protect your data, and outsmart cybercriminals before they hijack your identity and finances.
The Hidden Dangers of Cybercrime-as-a-Service: Protect Yourself Now!
Cybercrime-as-a-Service (CaaS) is making cybercrime accessible to anyone, even without technical skills. This growing threat enables malicious actors to easily access sophisticated tools and services for launching attacks. Learn how CaaS works and how to protect yourself from these evolving dangers.
The AI Security Storm is Brewing: Are You Ready for the Downpour?
The rapid integration of AI presents significant security risks for businesses and governments, from sophisticated cyberattacks and deepfake scams to data poisoning and privacy leaks. Understanding these evolving threats and implementing proactive mitigation strategies is crucial to navigating the complex AI landscape and safeguarding sensitive information.
When Strong Passwords Fail: Lessons from a Silent, Persistent Attack
Despite using a 36-character random password, my Microsoft account was nearly compromised. This post breaks down how persistent attackers operate, why strong passwords alone aren’t enough, and what IT pros can learn from my experience. A real-world wake-up call for anyone in cybersecurity.
Why the US Government is Considering a Ban on TP-Link Devices: A Deep Dive into IoT Cybersecurity and What It Means for You
The potential U.S. government ban on TP-Link devices has sparked cybersecurity concerns. This detailed document explores the reasons behind this move, the implications for IoT security, and what it means for consumers and businesses alike. Learn about the risks and what you can do to protect your network.
Cybersecurity for Beginners: Basic Skills
Master the fundamentals of cybersecurity with this beginner’s guide. Learn to identify indicators of compromise, investigate suspicious activity, analyze malware, and protect your system from evolving cyber threats. Start building your cybersecurity toolkit and stay informed to secure your data and devices effectively.
Why Password Managers are Essential for Strong Online Security
Password managers are essential for maintaining strong online security in today’s digital world. By securely storing passwords and generating unique ones for every account, they reduce the risks of breaches, ensuring your personal and professional data remains protected. Learn why using a password manager is a must.
Fake Tax Forms, Real Malware – How Cybercriminals Exploit Tax Season to Infect Your System
Tax season isn’t just for taxpayers—it’s prime time for cybercriminals, too. A new phishing campaign disguises malware as official tax forms, targeting unsuspecting users. Learn how these scams work, how to protect yourself, and why staying vigilant against tax-themed cyber threats is more crucial than ever.