998 words, 5 minutes read time.
In the fast-paced digital world, a major IT outage can cause widespread disruption and confusion. Recently, the cybersecurity company CrowdStrike faced a significant issue when a buggy software update impacted Windows computers worldwide. This outage led to a range of problems, from delayed flights to temporary business closures. Unfortunately, such events often create an opportunity for cybercriminals to exploit the situation.
Understanding the CrowdStrike Outage
CrowdStrike, known for its endpoint protection and threat intelligence solutions, released a routine software update that unexpectedly caused massive disruptions. The update, intended to enhance security features, contained a critical bug that rendered numerous Windows systems inoperable. As organizations globally rely on CrowdStrike for cybersecurity, the fallout was extensive, affecting various sectors including transportation, finance, and healthcare.
Technical Details of the Update Issue
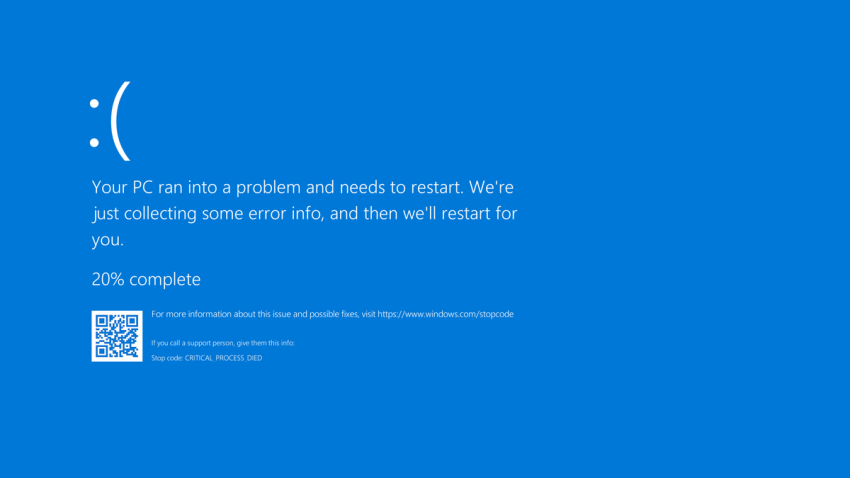
The problematic update included a configuration change to the kernel-mode driver, which is a critical component of the Windows operating system. This change inadvertently led to conflicts with certain system processes. When the updated driver attempted to interact with these processes, it triggered a condition that the system could not recover from, resulting in what is commonly known as the Blue Screen of Death (BSOD).
The BSOD errors occurred because the kernel-mode driver entered into an invalid state when attempting to execute certain commands, causing the system to crash to prevent further damage. This situation was exacerbated on systems with specific configurations and third-party software, which increased the likelihood of encountering the fatal error.
The Impact of the Outage
The immediate effects of the outage were severe:
- Delayed Flights: Airports experienced technical difficulties, leading to flight delays and cancellations.
- Business Interruptions: Many businesses faced temporary closures or significant slowdowns as their systems became unresponsive.
- Operational Chaos: IT teams scrambled to address the widespread issues, causing a ripple effect of delays and disruptions across multiple industries.
The Rise of Phishing Scams Following the Outage
Shortly after the CrowdStrike outage, reports emerged about a new wave of phishing scams targeting individuals and organizations. Cybercriminals are known to take advantage of major events, and this situation is no exception. By mimicking familiar events, they aim to deceive unsuspecting victims into clicking on malicious links or downloading harmful attachments.
How Scammers Are Exploiting the Situation
Scammers have become increasingly sophisticated in their tactics, using the CrowdStrike outage as a lure to trick people into compromising their systems. Here are some of the methods they are employing:
- Fake IT Support Websites: Scammers set up fraudulent websites that look like legitimate IT support pages. These sites claim to offer solutions for troubleshooting the CrowdStrike outage and promise to restore access to affected computers. However, instead of providing legitimate software updates, these sites host files laced with malware. Once downloaded, this malicious software can infiltrate your system, compromising your personal data and potentially causing severe damage.
- Phishing Emails and Text Messages: Cybercriminals send out emails and text messages that appear to be from trusted sources, such as your organization’s IT department or even CrowdStrike itself. These messages often contain urgent requests to download updates or click on links, which then lead to malware-infected downloads or phishing websites designed to steal your credentials.
- Social Engineering: Scammers use social engineering techniques to manipulate individuals into revealing sensitive information or performing actions that compromise security. This can include phone calls pretending to be from IT support, instructing you to download software or disclose passwords under the guise of resolving the outage issue.
- Exploiting Social Media: Cybercriminals may use social media platforms to spread misinformation and direct users to malicious websites. They may create posts or ads that claim to offer solutions for the outage, luring victims into clicking on dangerous links.
Tips to Protect Yourself from CrowdStrike-Related Scams
To ensure you don’t fall victim to these scams, here are some crucial tips:
- Be Wary of Fake Websites
The specific scam involves fraudulent websites claiming to provide solutions for the CrowdStrike outage. Always verify the authenticity of any website before downloading files or entering personal information. - Avoid Downloading Files from Unknown Sources
Whether it’s an email or a website, avoid downloading files or attachments unless you are certain of their legitimacy. For issues related to the CrowdStrike outage, contact your organization’s IT team directly for assistance. - Be Cautious of Urgent Communications
Cybercriminals often use urgency as a tactic to prompt impulsive actions. If you receive unexpected calls, emails, or text messages urging you to respond quickly, take a moment to assess the situation. Always verify the source before taking any action. - Stay Informed and Alert
Keeping up-to-date with the latest cybersecurity news and threats can help you stay one step ahead of potential scams. Be on the lookout for any suspicious activity related to the CrowdStrike outage or similar events.
Calls to Action
- Stay Vigilant: Stay alert and protect your digital life! If you suspect any phishing activity, report it to your IT department immediately.
- Avoid Downloading Files from Unknown Sources: Ensure your systems are up to date! Contact your IT team to verify that all security updates are properly installed.
- Learn More About Cybersecurity: Want to learn more about staying safe online? Subscribe to our newsletter for the latest cybersecurity tips and updates.
- Report Suspicious Activity: If you encounter any suspicious websites or emails related to the CrowdStrike outage, report them to your organization’s IT security team immediately.
- Check Before You Click: Remember: Think before you click! Always verify the source of any unexpected messages or links.
- Contact Us for Assistance: Need help with cybersecurity? Contact our support team for assistance and guidance on protecting your data.
- Follow Best Practices: Adopt best practices in cybersecurity. Download our free guide on how to protect yourself from phishing scams.
Conclusion
The recent CrowdStrike outage serves as a reminder of the ever-present threat of cybercrime. By staying vigilant and following these safety tips, you can protect yourself and your organization from falling prey to phishing scams. Remember, when in doubt, it’s always best to consult with your IT team or a cybersecurity professional.
Help Me Improve
I’d love to hear from you! If you have any tips, insights, or feedback on enhancing online presence and integrating digital strategies, please share your thoughts in the comments below. Your input is invaluable in helping me improve and provide more useful content. Thank you for contributing to the conversation!